






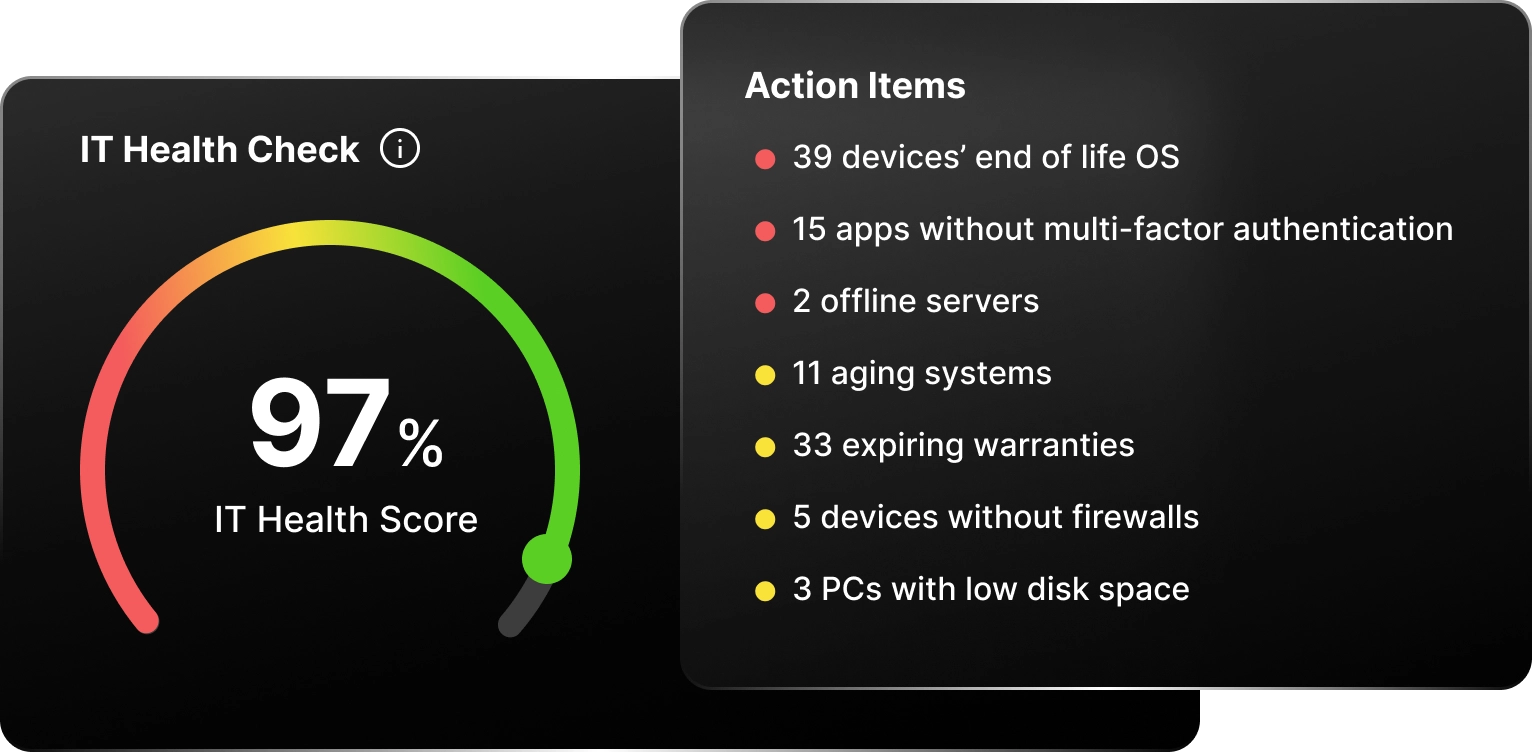
Our Managed IT services provide businesses with proactive and comprehensive IT support to ensure smooth and efficient operations. BlackPoint monitors your systems and identifies potential issues before they arise to minimize downtime.
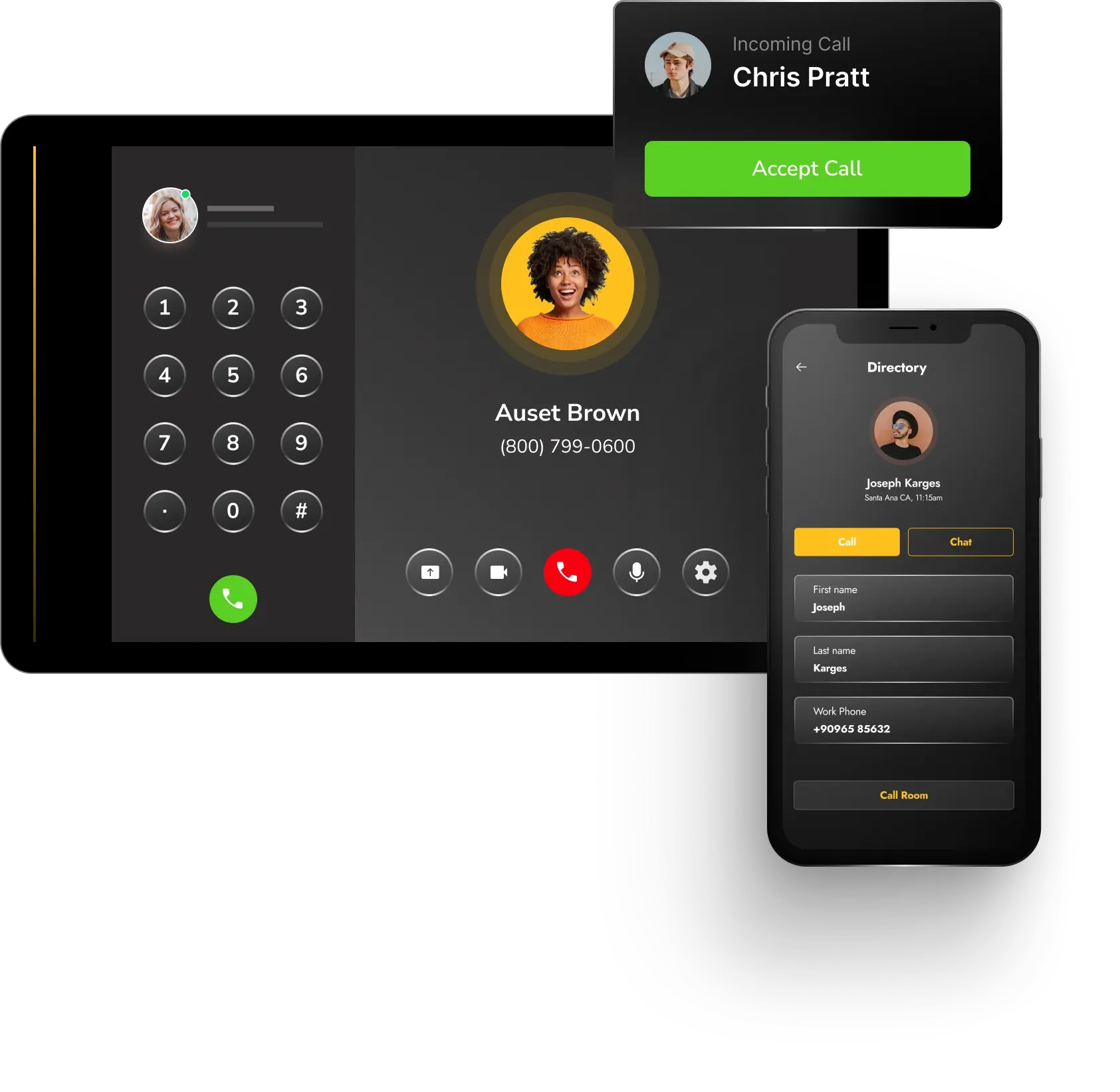
Improve business communication with flexible VoIP services that are easy to set up and integrate into your IT environment. BlackPoint’s hosted VoIP solutions save you money and provide efficient system management. Customizable contact center solutions improve customer engagement and streamline support. On-premises VoIP provides complete autonomy over your telephony setup.

The increasingly sophisticated threat landscape requires robust cybersecurity measures to protect your company’s valuable IT assets. BlackPoint’s comprehensive cybersecurity solutions provide continuous monitoring, threat detection, and incident response needed to keep your IT resources secure.
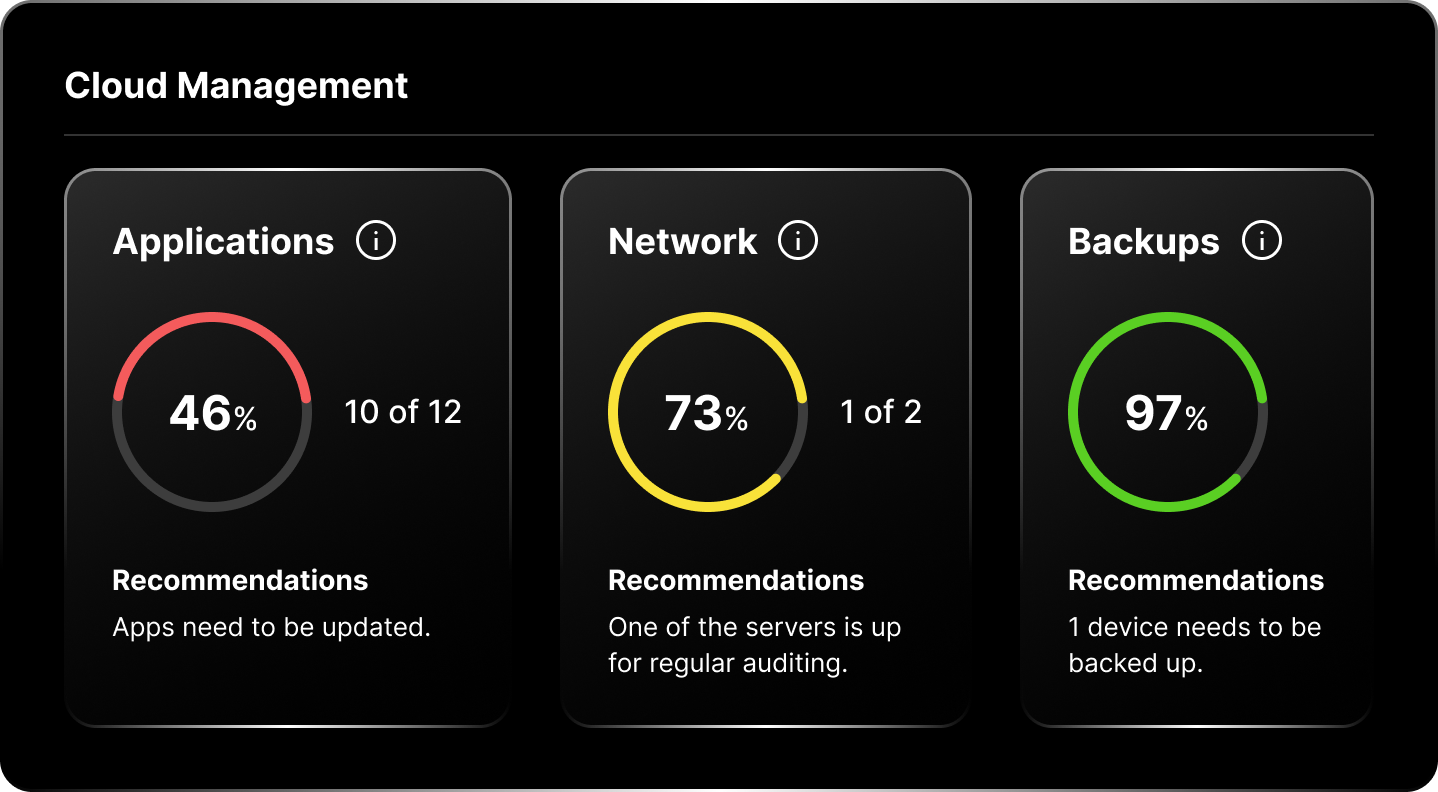
Managed cloud services enable your company to leverage the scalability, flexibility, and security of the cloud to address its unique business requirements. Our experts help you migrate applications and systems to the cloud and provide effective management — whether that's AWS, Azure, or your own private cloud.

IT consulting services provide businesses with expert guidance and advice on their technology strategy and implementation. BlackPoint’s experts manage your IT projects from end to end and offer customized solutions to address your business requirements.
hacks prevented
projects delivered
clients








Outsourcing your IT needs to an experienced Managed IT Provider offers your company with cost savings, scalability, and growth. BlackPoint offers advanced and effective IT solutions to enhance security, increase productivity, and optimize business operations.
BlackPoint understands the importance of securing your computing environment. We provide 24/7 monitoring and support, advanced threat detection, and effective response solutions to protect your valuable IT resources. You can call us anytime to resolve any issues.
We pride ourselves on maintaining excellent customer satisfaction with services that understand the importance of your IT environment by delivering prompt, knowledgeable, and on-point support for all your IT needs.
Our vCIOs with over 10+ years of experience help you with strategic planning and roadmapping that allows your in-house technical team to concentrate on new and value-added projects while you offload repetitive tasks to our IT support teams.
Leverage the wealth of knowledge and experience available from BlackPoint’s deep bench of IT professionals to grow and optimize your business.

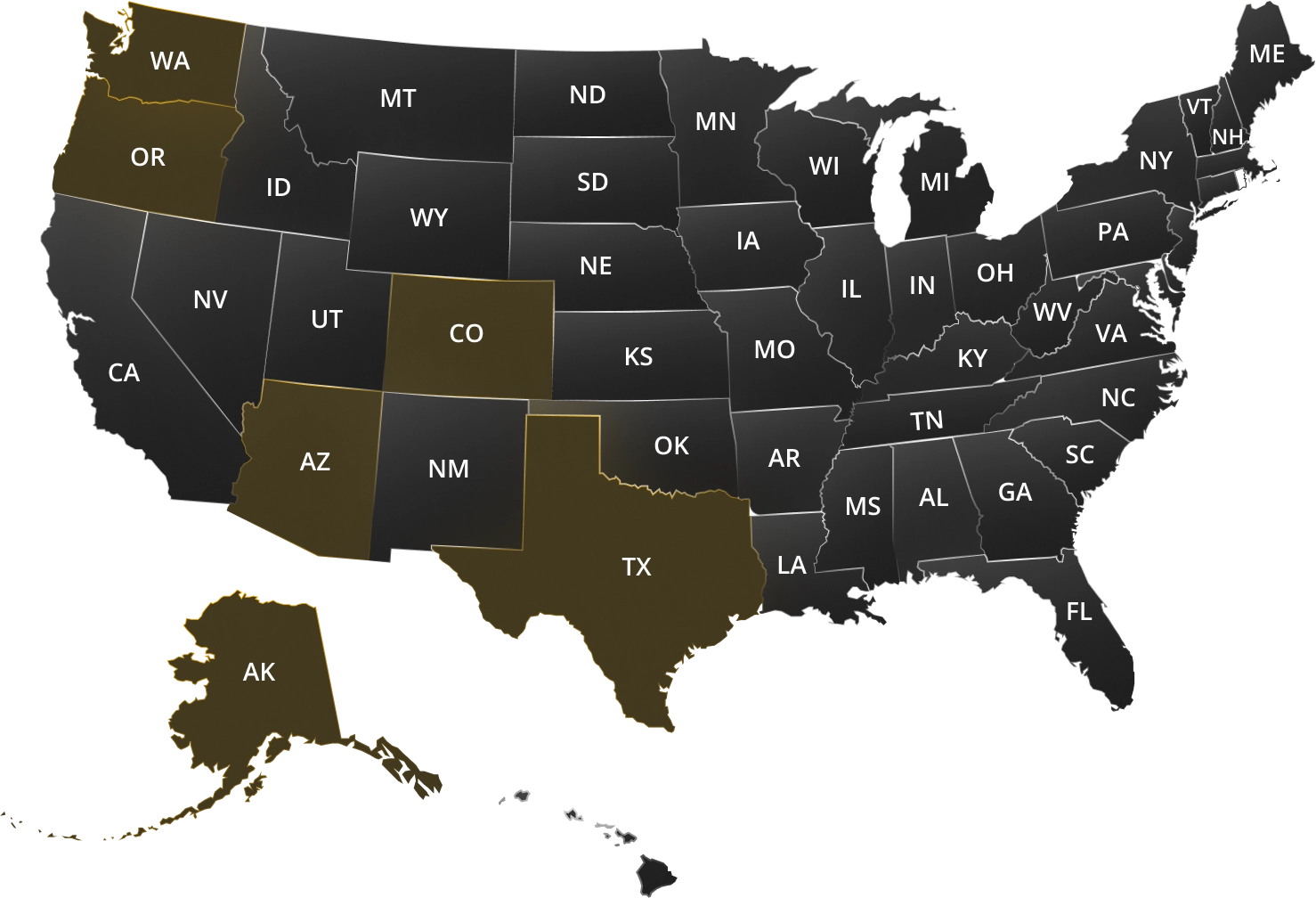
We provide comprehensive IT services and support to businesses across multiple locations, including major cities in Alaska, Arizona, Colorado, Idaho, Oregon, Texas, and Washington. Our team of IT experts can help you with managed IT services, cloud solutions, cybersecurity, VoIP services, telecom, and carrier services.
View Service AreasBlackPoint IT offers a 24/7 service desk to give clients immediate technical support whenever issues arise.
Our dedicated vCIO offers strategic IT solutions to help optimize and grow your business. We help your company make informed decisions regarding infrastructure components, software selection, cybersecurity solutions, roadmapping, and IT budgeting.
We provide continuous monitoring and real-time threat detection to quickly identify and address cybersecurity risks before they cause major damage to your environment.
Our regular patching, network, and server management ensure that all infrastructure components perform optimally for a smoothly running and efficient computing environment.
BlackPoint IT offers a client portal that allows our clients to easily request technical support, track the status of their tickets, and communicate directly with our team of expert technicians.
Yes. We use remote tools to accommodate our clients wherever they are.
Managed IT revolves around being proactive and preventing issues before they arise, while break/fix is more traditional—”you break your technology, we come and fix it for you”.
With the rise of cybercrime, a break/fix strategy isn’t feasible. Having a managed solution proactively prevents cyberattacks by keeping your systems up to date and secure.
We provide you with a comprehensive look at how your systems and infrastructure are functioning. First, we’ll schedule a 30-minute call with you to identify your goals in doing the assessment.
Once we’re aligned on the desired outcomes, we will conduct a penetration testing to identify your vulnerable and outdated systems.
Afterwards, we’ll discuss the findings and issues that need immediate attention.
For both consulting and managed IT, professionals help you determine the best business technology that fits your needs. However, in terms of the implementation of future technologies in the long haul, managed IT services can make them happen for you by developing a long-term relationship that keeps your technology working well every day.
Most organizations use managed IT services because modern cybersecurity and technology management are a pain in the neck. Securing your organization’s devices and network require constant attention at the most minuscule level on a daily basis.
Even if you have an in-house IT team to put out fires, it’s still not enough. Managed IT provides you with comprehensive technology management that ensures compliance and security across operations, including endpoint security, network security, cloud security, and policy management.
Get a custom quote based on your business requirements.